Tracking my daily progress for LeetCode challenges. This is a continuation of this post. The source code for these examples can be found on the GitHub repo. Dec 21 2023 – Widest Vertical Area Between Two Points Containing No Points Difficulty Level: Medium It should pass below test cases: class WidestVerticalAreaTest…
Author: Hoai Thu

Docker Essentials: A Novice’s Journey
In this post, I will share my personal notes on Docker when learning Microservices and Cloud Native architecture. It’s important to understand that this post is not a comprehensive guide but rather a collection of essentials about Docker. Learning isn’t just about reading, it’s about doing. Let’s kick off with…

Spring Cloud Gateway as an OAuth2 Client
In my previous post, I introduced the API Gateway Pattern in Microservices. Let’s take a look at the components in our system, as demonstrated below. We have API Gateway which proxies our requests to the authorization server and two services in our services. The API gateway has to proxy requests…

An Introduction to Prompt Engineering with LLMs
Last month, I accidentally discovered OpenAI APIs. It turns out that I’ve explored a ton of resources, and found inspiration. That’s why I decided to start with some short courses about LLMs, prompting, and building a system applying these APIs. This post serves as my compilation of notes from various…

A brief overview of API Gateway Pattern in Microservices
In my previous post, I introduced the process of building an authorization server, which serves as my starting point for delving into the world of microservices. In this post, I will go into the theory of the API gateway pattern. The implementation details for each function of it will be…

Implement OAuth using Spring Authorization Server – P2
In the previous post, I introduced two OAuth2.1 grants: client credentials and authorization code. In this part, I will walk you through the implementation of each grant using the Spring Authorization framework. Starting from Spring Security 5, the Spring team no longer supports building an authorization server from spring-security-starter but…

Implement OAuth using Spring Authorization Server – P1- A brief overview of OAuth2 and JWT
Last week, I set out to create an application based on microservices architecture, primarily for learning purposes. My initial focus was to secure the application, which led me to learn how to build a Spring authorization server from scratch. While I had previously implemented resource servers, building an authorization server…
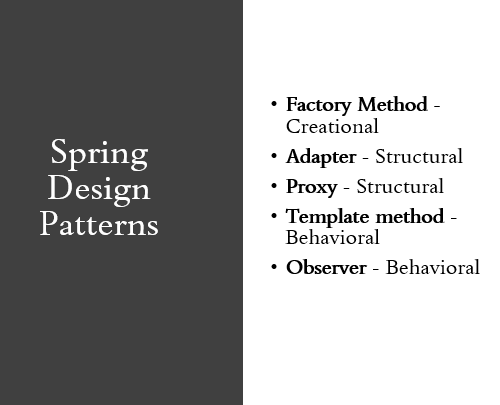
Spring Design Patterns
Design Patterns play a role in almost every aspect of the framework from its core. Operationally, Spring itself works using design patterns and supports your patterns in the process. In this post, I will go through Spring use cases where some well-known design patterns are applied. However, it won’t focus…
Spring IoC – Understand how Spring initializes beans
Spring is one of the most widely used Java EE frameworks. As with any framework, its utility grows exponentially once you understand its inner workings. At its core, Spring Framework is based on two design principles – Dependency Injection and Aspect Oriented Programming. This post is a note in my series which aims to explore the…

Data Normalization Explained – 1NF, 2NF, 3NF, 4NF
As I strive to expand my skill set, along with algorithms, I am focusing on honing my expertise in databases. In this post, I am going to find out the concept of data normalization, exploring its process through an example. In simple terms, data normalization is a set of rules…

